How Browsers Fight for Your Security
History
Web browsers have come a long way since 1990. The first one to be conceived was called WorldWideWeb (not to be confused with the abstract information space) and quickly renamed to Nexus. It was developed by Sir Tim Berners-Lee and was made for FTP file sharing, limited streaming services and to access Bulletin Board Services.
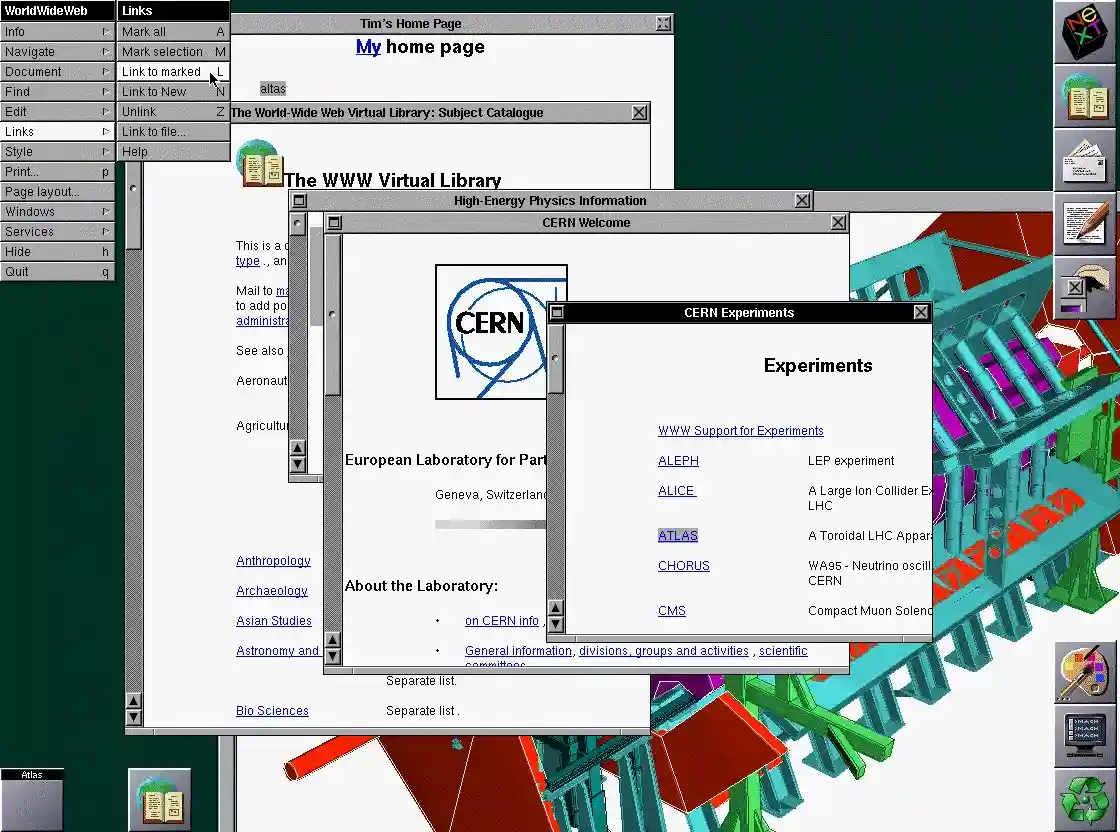
This is what Nexus looked like in 1990 (Source)
What followed can only be defined as an explosion of the internet and web browsers. From Mosaic and Lynx in 1993, followed by Netscape Navigator in 1994, Opera in 1995 and then the Internet Explorer 1.0 in August 1995, these pieces of software quickly became an integral part of every OS. In the mid 90s, Netscape was all the rage! But that browser had many first time features considered standard today. Here's some excerpts from their launch promo text:
- Free Browser: "Netscape Communications Corporation today announced that it is offering its newly introduced Netscape(TM) network navigator free to users via the Internet." (This shows how providing web browsers for free was a novel concept back then)
- Multiple Downloads: "The initial version of Netscape... enables users to ... multiple, simultaneous network accesses, allowing several documents or images to be downloaded simultaneously."
- Image Support: "Native support for the JPEG image format." (This highlights how supporting image formats like JPEG was an essential feature for a web browser) Netscape Communications News Release, 1994
After Microsoft started bundling Internet Explorer with Windows, Netscape gradually lost market share and would eventually go under. But they would go on to create the Mozilla Foundation which led to a browser still used by millions today - Firefox.
Did you know? Apple used Internet Explorer upto 2003, when it finally came up with Safari?
Google jumped into the race with Chrome in 2008. What stands today is the result of repeated stages of evolution of the software. It became so important for these megacorps that it led to browser wars. Today, using browsers you can :
- Retrieve + render content from the web and display it. This includes sophisticated web pages, pictures, streaming media and document formats like PDFs.
- Administer accounts, embedded systems or even web servers remotely.
- Create content with a number of services like Google Drive, Adobe Creative Cloud or Microsoft Office 365. These even do away with the need to store user data on your HDD and use the Cloud.

Interested in Browser Wars? There's is a whole podcast series from Wondery about it. You should give it a listen!
Security?
The ubiquity of web browsers in today's world, with over 5.3 billion users in 2023, makes them prime targets for attackers.
We certainly don't want this a norm.While security is paramount, vulnerabilities like same-origin policy breaches, session hijacking, XSS, and CSRF pose significant threats. Fortunately, modern browsers are equipped to detect and mitigate many of these issues, often stemming from server-side flaws, thanks to features like sandboxing. However, ongoing efforts are needed to address lingering access control inconsistencies.
Building a Wall of Defense
There's a lot going under the hood that protects you when you're online. We'll briefly go over some basic security requirements which ought to be fulfilled by each modern web browser:
- User Data Protection: Done by essentially separating local and session storage. Your browser does this based on protocols, domains and ports. Making sure each session's storage is accessible only from the originating window or tab and gets deleted once it closes.
- Provide an option for Cookie Blocking: Referring to third party cookies.
- Sandboxing rendering processes: There are certain restrictions that the browser must adhere to while it is rendering a web page or an application on your computer. For example - the process should only access part of the file system which is dedicated to your browser. It should also have reduced privileges with respect to other browser processes.
- Same Origin Policy : This one's really important. It means that your browser only permits scripts contained in a web page to access data in another web page iff both these pages are from the same origin.
- Secure cookies over HTTPS: It is your browser's responsibility to make sure that cookies containing a “secure” attribute in the header are sent over the HTTPS protocol.
- Alert the user if they're being tracked: Certain websites or PWAs require access to your geolocation, microphone, camera or notification preferences. As a user, you should always be informed if that's the case.
- Preventing automatic file executions: It makes sure no downloaded content is launched automatically. It also gives you an option to either save or discard downloaded files. [Note: this doesn't include any mobile code, scripts, or add-ons]
- Preventing loading of unsigned code: Your browser provides you with the option to discard unsigned, untrusted or unverified mobile code. These include ActiveX, (the now depreciated) Flash or Java.
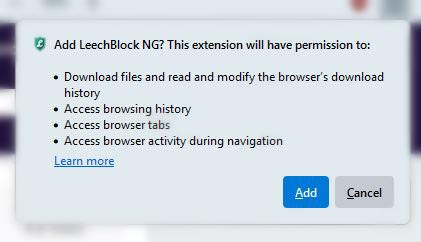
- Verifying addons: Your browser makes sure it can cryptographically verify extensions you download from the web store. Piggybacking on this point, it prevents automatic installation of add-ons (remember that small pop-up confirmation before installing a new extension)?
Conclusion
The possibility of an exploit always looms and it's a nagging reminder that even the most fortified software has its vulnerabilities. But among the 100s of headlines of clever attacks and zero-day exploits, it's easy to overlook the silent war being waged by developers on the frontlines of web security. Modern browsers, once simple portals to the web, have become intricate fortresses. They constantly evolve to contain the ever-shifting threat. While the web, like the software that navigates it, remains imperfect, it's worth pausing to acknowledge the silent guardians constantly working behind the scenes, keeping us safe in the digital world.
ps: Feel free to tag me on Mastodon if you have any thoughts or questions about this piece. I'm always eager to learn and appreciate diverse perspectives.